DevOps Engineer and Team Building Articles
Agile AI Automation AWS Azure Calmr Certification DevOps DevOps Engineer DevOps Tools Infrastructure as Code (IaC) Integration/Continuous Deployment (CI/CD) Resource Allocation Site Reliability Engineering Software Development Team Management Testing

Boost Your Development Teams Productivity By Using These Top Generative Culture Tools
In the bustling world of software development having a generative culture could be your secret […]

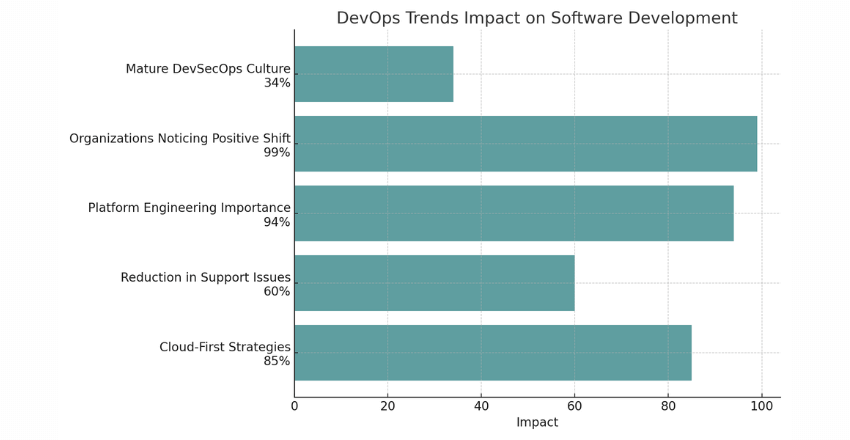
38 DevOps Statistics You Need to Know
Why bother with 2024’s DevOps statistics? They’re your ticket to staying sharp and ahead in […]

The DevOps Engineer’s Role in Software Delivery
DevOps is a relatively new IT culture that emphasizes collaboration and communication between development and […]

Scaling with Infrastructure as Code
As businesses grow, so do their infrastructure needs. Maintaining a scalable and efficient infrastructure becomes […]

Testing in DevOps: Strategies and Approaches
Did you know that according to recent industry analyzes, organizations that adopt DevOps testing methodologies are likely […]

DevOps Implementation Guide for Beginners
How to implement DevOps strategies effectively starts with integrating development and operations teams, prioritizing continuous […]

Realizing DevOps Benefits: Transforming IT
DevOps benefits organizations by merging development and operations, resulting in faster deployment, improved collaboration, and […]

Mastering DevOps: Essential Tools
DevOps Tools are the backbone of modern software engineering, enabling continuous integration, deployment, and monitoring […]